Create a project and credentials on Tower
In the second episode of our blogpost series we show you how to make Tower ready to run a couple of playbooks we prepared for you on Gitlab.
You need to set-up a project, which is a logical collection of playbooks. You can create a project directly on the server and put it in a predefined directory, like /var/lib/awx/projects/. However, it is better to use a versioning system like Mercurial, Subversion or Git. We prepared some playbooks for you on Gitlab.
Let’s go! Login to your Ansible Tower:
1. Create a Project
First, create a project on Tower. A Project is a logical collection of Ansible playbooks, represented in Tower. We stored all the playbooks used in this Lab in a GITLab repository. We’ll add this repo to the project.
In Ansible Tower, click on RESOURCES/Projects and then the + ADD – button to create a new project. In the DETAIL tab, fill in the following fields:
NAME: Azure Deployment OKD
ORGANIZATION: Default
SCM TYPE: Git
SCM URL: https://odyssey.devoteam.be/publicOKD/deployOkdAzure.git
SCM UPDATE OPTIONS: check the Clean and only the Clean checkbox.
You don’t need a SCM CREDENTIAL, because this repo is public.
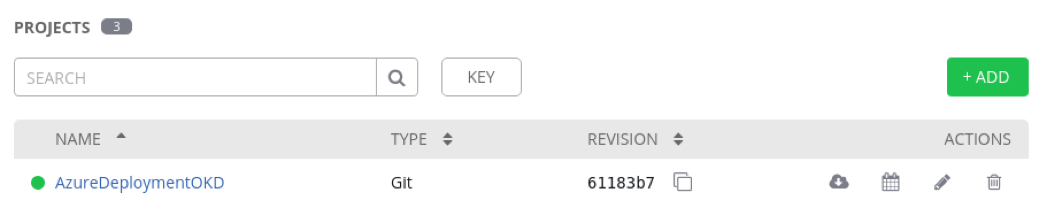
The dot before AzureDeploymentOKD should be green, meaning the repo synced just fine. You can click on the cloud-icon to force a new synchronisation. If you click on the dot, you will see the details of these actions. In the STANDARD OUT screen, you’ll see that Ansible Tower uses a playbook to sync the repository from GitLab.
2. Create ssh-keys on your computer
The next step is to create a key, so that Tower is able to communicate with the virtual machine we’ll deploy.
Create a ssh key on your local machine. Generate your ssh key-pair. For this exercise, do NOT specify a passphrase and accept all the defaults.
- Create the private key:
$ |
ssh-keygen -f ~/towerLabKeyPrivate |
Do NOT enter a passphrase.
To copy the PRIVATE key, you can use cat:
$ |
cat ~/towerLabKeyPrivate |
- Create the public key:
$ |
ssh-keygen -y -f ~/towerLabKeyPrivate > ~/towerLabKeyPublic |
To copy the PUBLIC key, you can use cat:
$ |
cat ~/towerLabKeyPublic |
3. Create credentials in Tower
Tower utilizes credentials for authentication when launching Jobs against machines, synchronizing with inventory sources, and importing project content from a version control system.
You can grant users and teams the ability to use these credentials, without actually exposing the credential to the user. If you have a team member moving to a different team or leave the organization, you don’t have to re-key all of your systems just because that credential was available in Tower.
Click on RESOURCES/Credentials.
A Machine credential is necessary to make it possible for Tower to connect to the VM’s we will deploy. You need the private ssh key for this.
$ |
cat ~/towerLabKeyPrivate |
To view the key, copy this to your clipboard:
Click on the + ADD button.
NAME: clusteradmin
CREDENTIAL TYPE: Machine
TYPE DETAILS:
USERNAME: clusteradmin
SSH PRIVATE KEY: < paste id_rsa >
You may leave all other fields empty.
Save
The Key is now encrypted and only Tower can access it.
4. Create inventories
An inventory is a collection of hosts managed by Tower. Ansible Tower 3.2 introduces the ability to choose an inventory file from source control, rather than creating one from scratch.
This function is the same as custom inventory scripts, except that the contents are obtained from source control instead of editing their contents browser. This means, the files are non-editable. As inventories are updated at the source, the inventories within the projects are also updated accordingly, including the group_vars and host_vars files or the associated directory.
In Tower click on RESOURCES/Inventories.
You need two inventories. The localhost inventory will be used by our playbook 1. Beside this localhost we need one more inventory, one for playbook 2 and 3. These inventories will be dynamically updated by the first playbook we run, therefore we use a source.
Click on the + button, and choose Inventory in the DETAILS Tab:
NAME: localhost
ORGANIZATION: Default
Save
In the HOSTS tab click on the + button.
HOST NAME: localhost
Save
The localhost inventory is created. Now we need one more inventory.
Click on the + button and choose Inventory in the DETAILS Tab:
NAME: okd
ORGANIZATION: Default
Save
In the SOURCES Tab.
Click on the + button.
We use a SOURCE in order to update the INVENTORY dynamically.
NAME: okd
SOURCE: Sourced from a Project
PROJECT: Azure Deployment OKD
INVENTORY FILE: inventory/hosts (This is not in the dropdown you need to enter it!)
VERBOSITY: 2 (DEBUG)
UPDATE OPTIONS:
flag: Overwrite, Overwrite variables, Update on Launch
Later, this inventory will be used by playbook 2 and 3.
Save
Please note that this new Inventory isn’t able to synchronise yet, because the chosen files are empty at the moment. They will be updated by our first playbook.
What’s next?
This blog post is part of the series “Using Ansible Tower to deploy OpenShift on Azure: a step-by-step guide”. In the next episode we’ll create our first job template in Ansible Tower. This template will use a playbook that installs the virtual machines needed for OKD in Azure.
