Recently, we wrote a blog with 3 short-term basic tips for ransomware prevention. The reason was the heightened threat-level due to the current crisis. Many organisations were scrambling to enable remote working, leaving their IT-environments vulnerable, and many malicious e-mails and websites used COVID-19 news, statistics or information as clickbait.
The basic tips in that first blog required little or no new technology and were meant to tackle the most glaring weaknesses right then, right there. This new blog is about the next step: How to mitigate the risk of ransomware via a phased approach that respects your budget.
what could possibly go wrong?
So first things first, why re-examine your ransomware prevention measures and policy? Here’s three reasons:
- In the field, we notice a strong focus on measures that protect critical workloads first and most. This is mainly because of the delicate balance between critical and supporting technologies. And it’s not wrong either, it’s just important to know that the root of the problem is often not where you feel the pain. Ransomware, attacks on your core processes or major data leaks mostly find their way into your organisation through simple e-mails, shadow-IT or a wrong click on the internet.
- Investments in ransomware prevention often do not reflect the tried & tested principles of IT Security:
 These principles have been around for years, and everyone knows them. But striking the right balance and finding the right expertise is not easy. A thorough approach to ransomware prevention requires an effort on every front.
These principles have been around for years, and everyone knows them. But striking the right balance and finding the right expertise is not easy. A thorough approach to ransomware prevention requires an effort on every front. - Ransomware prevention is led by IT, and that means it’s easy to get caught up in sophisticated technology. All too often, it’s a challenge to actually take on people and processes with the same level of scrutiny. Detecting and containing threats with a ‘Security Operations Center’ (SOC), ‘Endpoint Detections and Response’ (EDR) and ‘Security Orchestration, Automation and Response’-stack (SOAR) is definitely sexy stuff, and required in the end. But it’s worth noting that they are not effective if you don’t master the basics. A lot of damage can be prevented, for example by optimising the off-boarding of employees. Or by patching your firewall sooner. Or by simply teaching Linda not to click on any link in her incoming emails.
taking ransomware prevention to the next level.
In order to set up and run an effective ransomware prevention, a phased approach is absolutely crucial. By taking it step by step, you can make sure your priorities are met, best practices are followed and the balance of measures is right. At Devoteam we use a levelled approach, in which we optimise and streamline security in different phases.
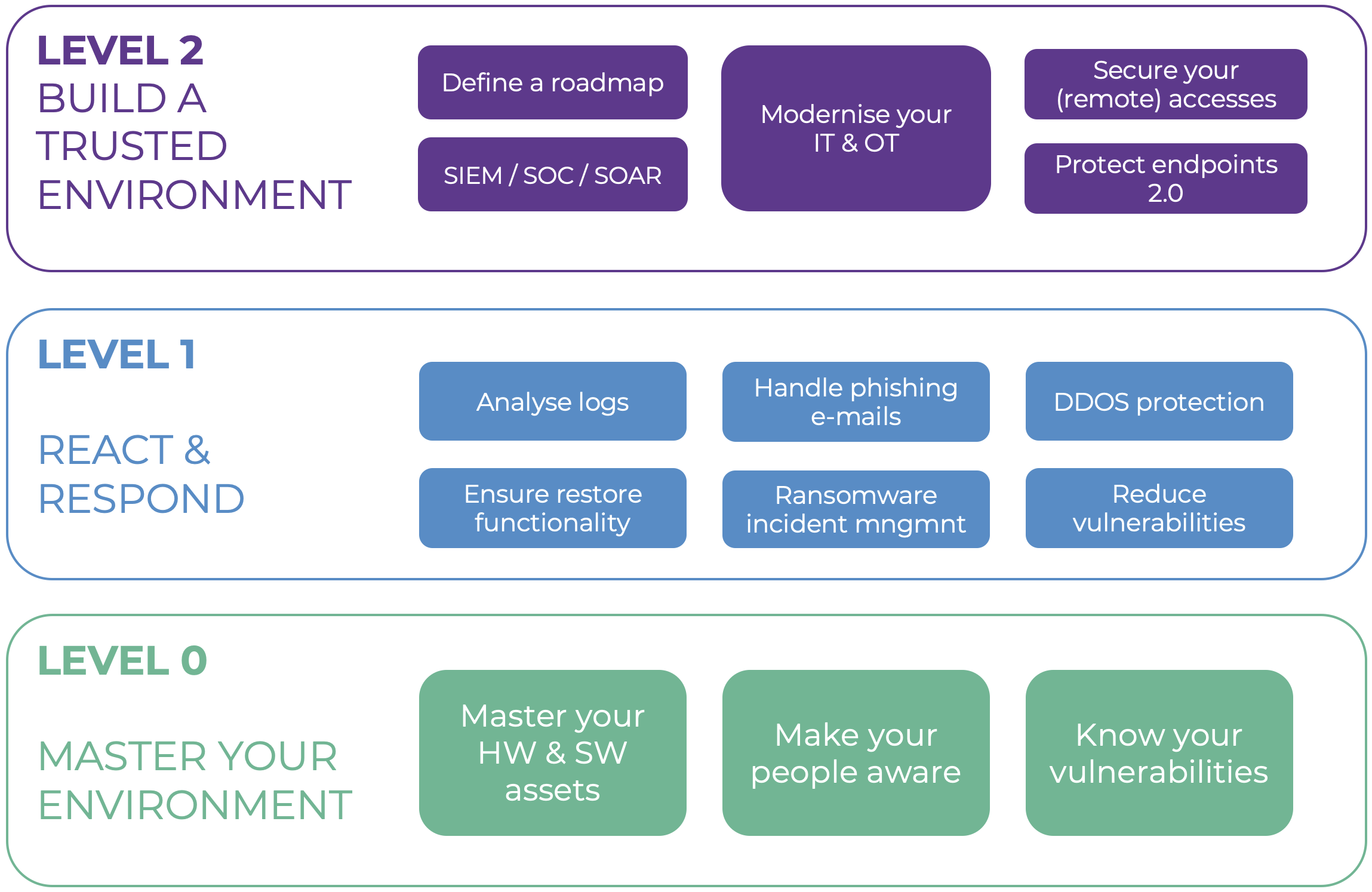
LEVEL 0: MASTER YOUR ENVIRONMENT
In order to provide adequate security, it’s essential to map out your entire environment, including workflows, processes, technology, endpoints and policies. You can do this manually or automated, as long as it’s up to date and complete.
When this is done, take a look at your users: what’s their level of awareness, what risks do they take and how do they work? You need to create awareness among your users. After that, you’ll have clear insight into your known, unknown and common vulnerabilities.
LEVEL 1: REACT & RESPOND
At this level, you need to start investing in basic respond and correct capabilities. With relatively simple tools for e-mail security, DDOS protection or ransomware incident management, you tackle your main priorities and reduce your risks.
Based on your vulnerabilities, you prioritise your first countermeasures. Do you need additional e-mail security software? Do you need to expand back-up and recovery capabilities? Or is ransomware incident management your main focus?
LEVEL 2: BUILD A TRUSTED ENVIRONMENT
Now it’s time for the big guns. And in order to align your measures to your security roadmap, it is essential to build a roadmap. Diving head first into SOC or ‘Security Information and Event Management’ (SIEM) will lead you to neglect other crucial aspects of your security.
You set up policies and you roll out the tools to enforce them. The tools and solutions in this level are focused on correcting and containing threats. Want to get started with zero trust networks, privileged access policies or ransomware incident management? Good. But make sure you’ve got the rest covered too. Stick to your roadmap and take it step by step.
