All our customers are now rapidly expanding what they’re doing in the cloud, mostly in a cost-effective hybrid set-up. According to Forbes, 83% of enterprise workloads will be in the cloud by 2020. But although working in the cloud has clearly become the standard approach, there is still considerable confusion about who has ultimate responsibility for the security of cloud infrastructure and applications. It must be the cloud provider, mustn’t it?
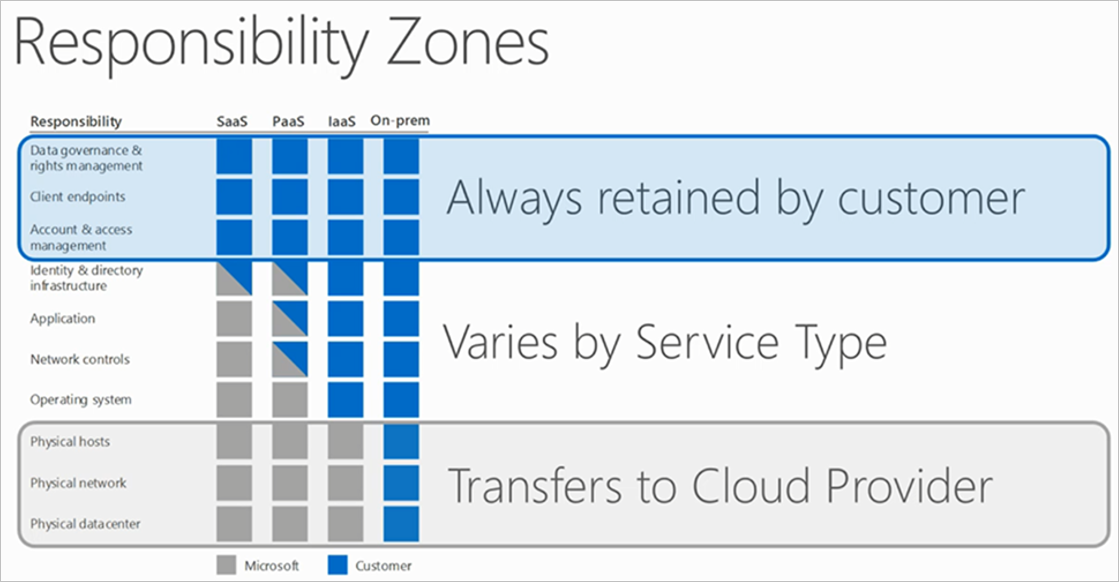
Indeed, it is the cloud provider, but that’s just part of the answer. You’re responsible too. Cloud security is always a shared responsibility. Some of the responsibility lies with the cloud provider, some lies solely with you and the rest needs to be discussed, depending on the circumstances and the type of service you require. Microsoft – for whom we are a strategic partner – has published a crystal-clear graphic (see below) that shows what it calls the ‘responsibility zones’ for complete Azure infrastructure security.
IaaS, PaaS, SaaS
The cloud provider is always responsible for physically protecting the data centre, the network and the hosts. Your responsibilities depend on what type of cloud services you’re purchasing. If you opted for an IaaS model, you are responsible for everything else. On the other hand, if you chose a standard SaaS model then your cloud provider takes responsibility for the security of the operating system, the network controls, the application itself and the directory infrastructure. Working with a PaaS model comes somewhere between IaaS and SaaS, depending on your agreement with your cloud service provider.
 Source: https://docs.microsoft.com/en-us/azure/security/azure-security-infrastructure.
Source: https://docs.microsoft.com/en-us/azure/security/azure-security-infrastructure.
Whatever your model, you are always responsible for data governance and rights management, endpoints, account and access management. Please don’t take the security of these elements for granted just because you’re working in the cloud.
Security roadmap
Security is part of our standard offering, so we’re happy to help you out. When we secure your hybrid cloud computing operations, the starting point is a security roadmap, often mapped to ISO/IEC 27001 control policies. We always work according to guidelines such as the CIS 20 Critical Security Controls, SOC or best practices for the GDPR. We may work on a business-oriented cloud roadmap first, depending on your needs. Then we start a technical project to implement the appropriate series of security solutions and align this with an adoption track. In addition to our proven expertise in everything related to Microsoft security, we also pride ourselves on our partnerships with CyberArk (privileged access management) and ForgeRock (identity management), because these enable us to bring a very high level of overall security to the Azure, O365 or Hybrid Cloud platform.
During the project, we regularly review your security plan, check where we are against the CIS 20 controls or another set of best practices, provide an awareness campaign with training and security games, and automate for continuous auditing.

 Interested in discovering in more detail what we can do to bring your cloud security up to standard and raise security awareness in your organisation? Then please contact Joey Bergen via
Interested in discovering in more detail what we can do to bring your cloud security up to standard and raise security awareness in your organisation? Then please contact Joey Bergen via