Securely protecting your data
Today’s world is data oriented. The IT department has to change and evolve its posture, from a perimeter security approach to a data-centric approach in order to ensure data security. IT Risk & Security expert Raphaël Dropsy dedicated two tech blog posts to this topic. Here you can read the first one, that focuses on understanding your data. You can read the sequel below. We’ll talk other remaining challenges that you must take into account to securely protect your data – such as data security technology, legal & regulatory requirements and information governance.
Just a quick refresher: a data lifecycle is the sequence of stages that a particular data unit goes through, from its initial generation or capture to its eventual archival and/or deletion at the end of its useful life. It represents the phases the data goes through, from creation to removal. Data lifecycle has already existed for a long time, but cloud computing brought new challenges.
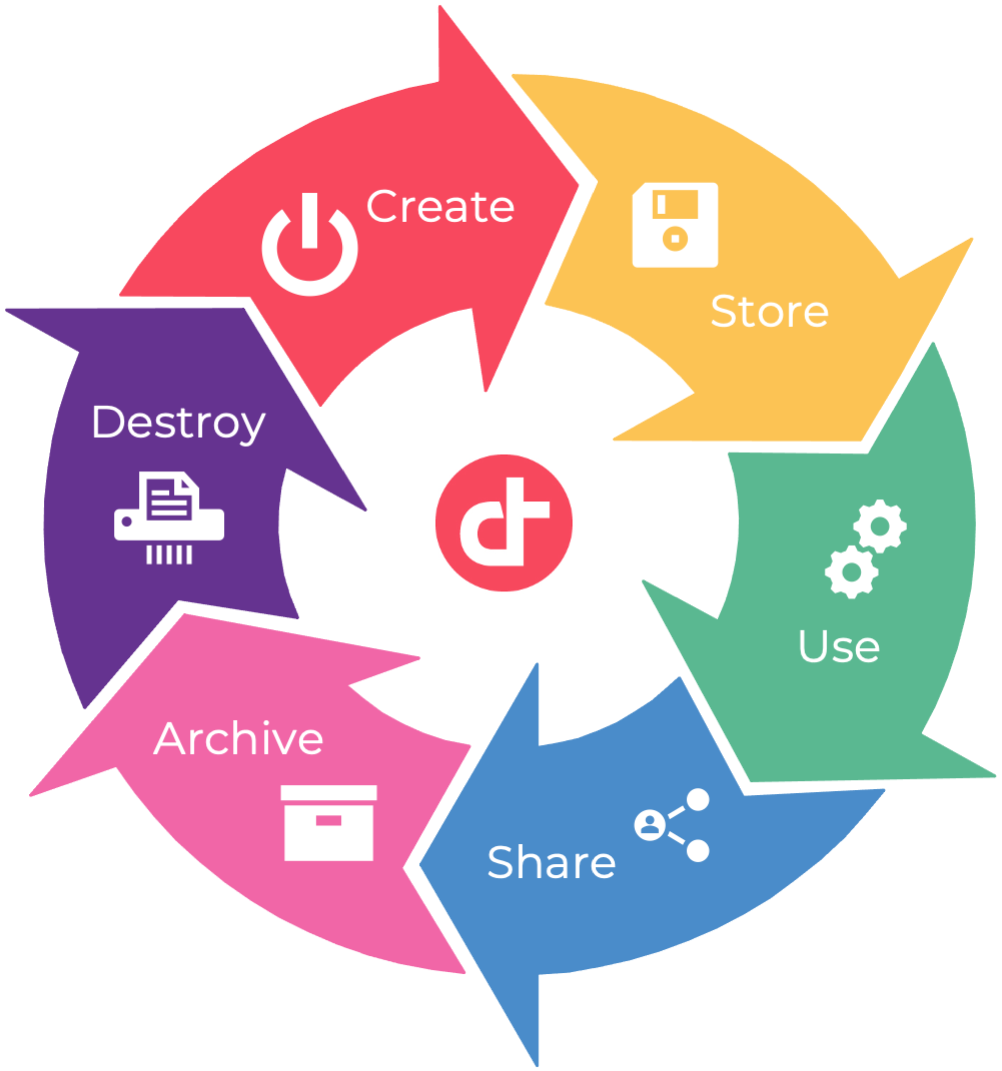
After our first blog post, you should have learned how to understand your data. Now let’s have a look at how to securely protect your data.
Relevant data security technologies
The goal is to ensure Confidentiality, Integrity and Availability (CIA) of data by deploying controls.
- DLP (Data Leak Prevention): prevent unauthorised exfiltration and meet regulatory requirements. Architecture (Network or Endpoint DLP) depends on the data’s state (data in use, in motion or at rest) and the threats you need to address
- Encryption: prevent unauthorised data viewing. Encryption Mechanisms (IPSec, VPN, TLS/SSL, Information Rights Management, Data Rights management) depend on the data’s state (data in use, in motion or at rest; long-term or short-term storage)
You should address the management of encryption keys: depending on who holds the keys – Cloud Service Provider, Cloud Service Consumer or third party provider – not all threats are mitigated.
- Obfuscation, anonymisation, tokenisation, masking: provide confidentiality. Used as alternative to protect data where encryption mechanisms can be unrealistic for performance, cost and technical abilities.
Legal requirements and privacy act
In your journey to understand and protect your data, you need to identify the law and legal requirements applicable to your organisation.
Depending on the type of your cloud service model (IaaS, PaaS, SaaS), you should understand the shared responsibility model between the Cloud Service Consumer and Cloud Service Provider. The first has much more responsibility when using IaaS than using SaaS. But in all cases, the Cloud Service Consumer is ultimately responsible for the data placement in the cloud and its access.
As mentioned, data in the cloud tends to replicate and move. So the data’s location may bring potential regulatory, contractual and other jurisdictional issues, depending on the cloud provider’s geographic location.
Information governance
Finally, an important aspect of your journey is to understand and protect your data: data governance. It includes the policies and procedures for managing information/data usage and strengthens controls.
It includes the following key features:
- Information classification: high-level descriptions of important information categories. The goal is to define high level categories like “regulated” or “trade secret” to determine which security controls may apply
- Information management policies: to define what activities are allowed for different information types
- Location and jurisdictional polices: where data may be geographically located
- Authorisations: define which types of employees/users are allowed to access which types of information
- Ownership: decide who should ultimately be responsible for the information
- Custodianship: who is responsible for managing the information, at the bequest of the owner
- Retention procedure: define retention period. This depends on laws, regulation and standards requirements
- Deletion procedure: define the rule to properly remove/destroy data. This is the physical destruction of the hard drive, degaussing and overwriting. Crypto shredding is the only reasonable method applicable for a Cloud Service Consumer to delete/remove data from the cloud and consisting in encrypting the data to dispose and destroy the encryption key
- Archiving procedure: define rules to archive/retrieve data. It should include the data format and media type, backup and recovery options, encryption, monitoring, eDiscovery and granular retrieval
To summarise
To secure your data, you need to build a strategy and include considerations related to the cloud computing. The most important steps are:
- Understand
-
- data type (regulated, PII, business, commercial)
- structure and format
- cloud service model
- cloud storage options
- location, movement & access
-
- Consider data access, data location, performance when dealing with the cloud
- Define ownership
- Understand the threats you would like to mitigate
- Plan
-
- data discovery, classification, labelling
- deployment of controls
- ongoing monitoring
-
